How to Access the VPOL Online Learning Data
The Vice Provost Office for Online Learning facilitates the teaching
of online classes. The instruction delivery platforms are instrumented
to collect a variety of data around students' interaction with the
study material. Examples are students manipulating video players as
they view portions of a class, solution submissions to problem sets,
uses of the online forum available for some classes, peer grading
activities, and some demographic data. The type of data that is
collected depends on the delivery platform used for a particular
class.
VPOL makes some of this data available for research on learning
processes, and for explorations into improving instruction.
All data that VPOL shares is available on machine
datastage.stanford.edu. You have multiple methods of using this data:
We provide self service answers to frequent questions, customizable to
your context. Data viewing programs for MAC and Windows allow you to
browse through our content. Going further, most analysis tools, like
R, SPSS, and Excel can connect directly to our databases. Similarly,
visualization tools are available that allow you to create static, or
interactive charts of data directly from our sources. We explain these
access methods here, or point to relevant instructions on the Web.
Additionally, we run
a Tableau Server
to which you can publish visualizations you create with the Tableau
Desktop visualization tool. Visitors can manipulate these
visualizations to the degree you provide for. A comment area is
available for each view to discuss the information. If desired, access
to the views can be limited. Again, more in this document.
We now run through the available access paths to the data, ordered in
increasing power (and sometimes associated complexity).
Access Bureaucracy
Even though we do not keep highly sensitive information on this
server, we do need to protect the data to some degree from malicious
intrusion. The precise procedure is being worked out. But the result
will be a user name, and either one, or two passwords for you. One
password if you are only to access data that does not reveal the
identity of the student that the data talks about. If you are
permitted to access more sensitive information, then you will receive
a second password. Appendix B explains the
technical background of these two cases.
In the following we assume that you have the necessary items in hand.
If We Anticipated your Question
In the simplest case your question has been asked and answered before,
albeit for a different context. Such a context might be a particular
class for which the question was originally asked, or a particular
problem set. For cases like this
our AnswerServer
might help. This server differs from a typical FAQ list in that you
are able to adjust the question to your context. We will be growing
the coverage of that page as we go along. If you have an idea for a
useful one-liner question, please send email
to .
Analysis Tools
If you need to perform analysis over the data, Excel, R, and SPSS are
among the tools that can access our data directly. After some setup,
the data appears in your table. After that setup, you are in your home
territory of the tool you are used to. This section explains how to
accomplish this data import.
The All-Important Database Connector
For all these connections, you will need a 'database connector,'
sometimes called an 'ODBC driver.' These drivers are set up just once
in your machine---Mac or Windows. To grab one of them, head over to
the MySQL
connector download page, and download the version for your
operating system (Windows or Mac). Note that even though your computer
might be of the '64 bit' type (whatever that means), you are likely to
need the 32-bit version of the database connector! This choice is
definitely the right one for Macs; for Windows it is the most likely
choice
(see why).
You start the downloaded program as you usually do on your
computer. Here is information you will need for the mostly-open data:
Server: datastage.stanford.edu
User: [your username]
Password: [your password]
Database: [see appendix A for the list of available databases]
Once you installed the connector, you will find it popping up in all
the right places among the menu options that are referred to in the
following sections.
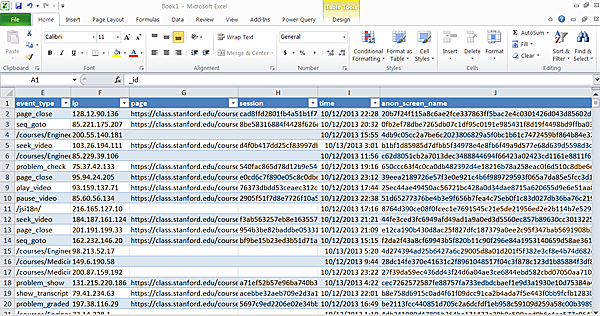
Connecting Excel
See this reference
for how to fill your spreadsheet with a particular dataset. The result
will look like this:
 For the phase in the above referenced instructions that looks like
this:
For the phase in the above referenced instructions that looks like
this:
 ... the information you enter will depend on whether you will be
accessing more restricted information, or the mostly open data.
Open data:
Data source name:
Description: [a reminder for yourself]
Server: datastage.stanford.edu
Port: 3306
User: [your user name]
Password: [your password]
Database: [the name of the database of
interest. See Appendix A].
... the information you enter will depend on whether you will be
accessing more restricted information, or the mostly open data.
Open data:
Data source name:
Description: [a reminder for yourself]
Server: datastage.stanford.edu
Port: 3306
User: [your user name]
Password: [your password]
Database: [the name of the database of
interest. See Appendix A].
Connecting SPSS
Here is how you connect an SPSS sheet to one of the VPOL data
sources. Remember first to install your database connector.
In SPSS:
File-->Open Database-->New Query
Assuming you have set your connector to point to database Edx,
and that you named it MonoEdx (for whatever fanciful reason),
you will then see this:
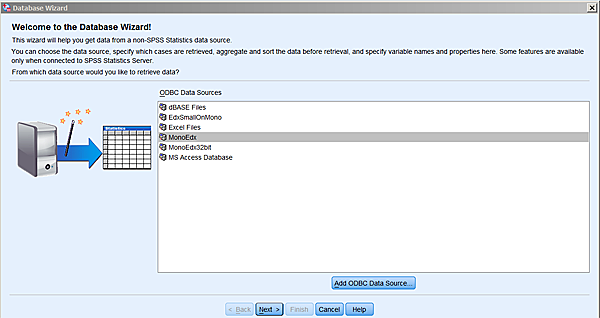 Choose whichever real name you gave your connector, and
click next. You now get to choose the fields that you want to
extract from the database:
Choose whichever real name you gave your connector, and
click next. You now get to choose the fields that you want to
extract from the database:
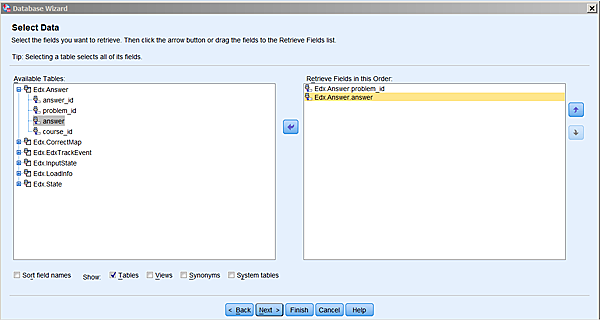 SPSS has figured out which tables are available in this database, and
you can start moving fields over to the right. Once you again clicked
on next, you will have an opportunity to introduce conditions
on which rows you would like to import:
SPSS has figured out which tables are available in this database, and
you can start moving fields over to the right. Once you again clicked
on next, you will have an opportunity to introduce conditions
on which rows you would like to import:
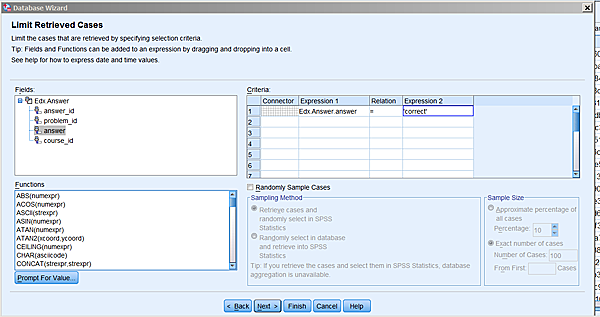 I am still a bit puzzled by the interface of this screen. If you get
stuck, we can try to figure it out. If all goes well, you will now see
something like this:
I am still a bit puzzled by the interface of this screen. If you get
stuck, we can try to figure it out. If all goes well, you will now see
something like this:
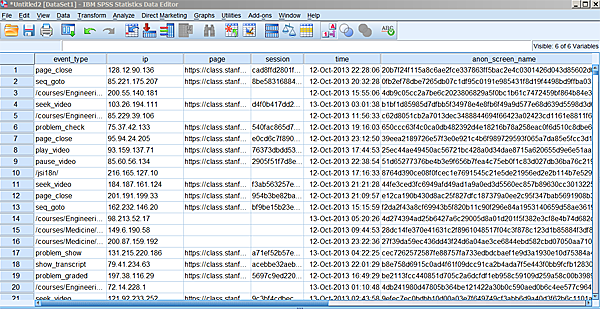
Browsing and Querying the Data
A number of applications are available for browsing data stored in
MySQL databases, the type in which VPOL data resides. Some
applications
are discussedon
the
Web. Froq
for Mac, and RazorSQL for Mac,
Linux, and Windows are freeware tools used in the VPOL group.
RazorSQL
The application RazorSQL, which works under Mac, Windows, and
Linux, can create either a tunneled or a direct connection to
MySQL. For details on the difference, please
see Appendix B. You begin the connection process
by choosing:
File-->New Tab (no connection)
In the subsequent screen, you click on Click to connect to a
database:
 ...resulting in:
...resulting in:
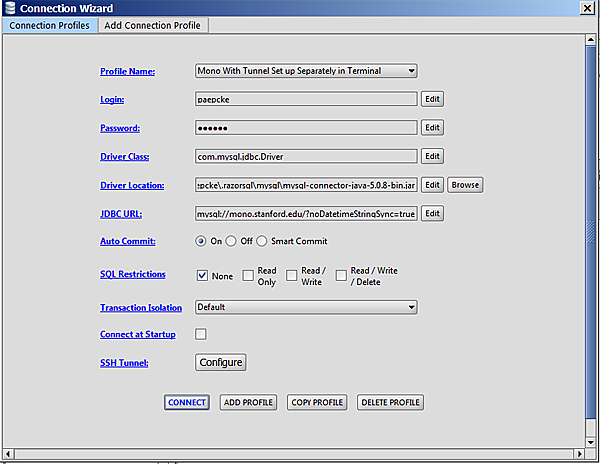 This screen allows you to select among different connections you have
already defined. Not having defined any, you click Add Profile,
and pick MySQL from the resulting list of database types that
the application knows about.
This screen allows you to select among different connections you have
already defined. Not having defined any, you click Add Profile,
and pick MySQL from the resulting list of database types that
the application knows about.
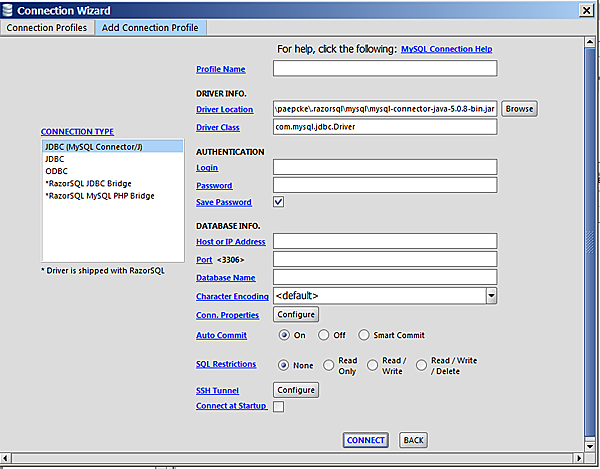 Here is where you fill in the particulars. Leave all pre-filled fields
alone. For Profile name you pick any name that reminds you
later of what this connection is about.
Login and Password are the information you received with
your access material. For Host or IP Address you fill in
datastage.stanford.edu. The Port is left
blank. In the Database field you enter one of the databases of
Appendix A. Click Connect, and you
(hopefully) see a screen other than one informing you of failure.
At this point, you can continue via the RazorSQL manual and help
pages.
Here is where you fill in the particulars. Leave all pre-filled fields
alone. For Profile name you pick any name that reminds you
later of what this connection is about.
Login and Password are the information you received with
your access material. For Host or IP Address you fill in
datastage.stanford.edu. The Port is left
blank. In the Database field you enter one of the databases of
Appendix A. Click Connect, and you
(hopefully) see a screen other than one informing you of failure.
At this point, you can continue via the RazorSQL manual and help
pages.
Appendix A: List of Available Databases
Course-to-Go Hosted Databases
c2g-db_winter_2013_forum
c2g-networking_fall2012_forum
c2g-solar_fall2012_forum
Coursera Hosted Databases
coursera-20130421-2305-12feb-gametheory_anonymized_forum
coursera-20130421-2305-12feb-gametheory_anonymized_general
coursera-20130421-2305-12feb-gametheory_hash_mapping
coursera-20130421-2305-12feb-gametheory_unanonymizable
coursera-20130421-2305-12jan-algo1_anonymized_forum
coursera-20130421-2305-12jan-algo1_anonymized_general
coursera-20130421-2305-12jan-algo1_hash_mapping
coursera-20130421-2305-12jan-crypto_anonymized_forum
coursera-20130421-2305-12jan-crypto_anonymized_general
coursera-20130421-2305-12jan-crypto_hash_mapping
coursera-20130421-2305-12jan-pgm_anonymized_forum
coursera-20130421-2305-12jan-pgm_anonymized_general
coursera-20130421-2305-12jan-pgm_hash_mapping
coursera-20130421-2305-12jan-pgm_unanonymizable
coursera-20130422-0245-12jan-ml_anonymized_forum
coursera-20130422-0245-12jan-ml_anonymized_general
coursera-20130422-0245-12jan-ml_hash_mapping
coursera-20130422-0245-12jan-ml_unanonymizable
coursera-20130422-0337-12feb-cs101_anonymized_forum
coursera-20130422-0337-12feb-cs101_anonymized_general
coursera-20130422-0337-12feb-cs101_hash_mapping
coursera-20130422-0459-12mar-automata_anonymized_forum
coursera-20130422-0459-12mar-automata_anonymized_general
coursera-20130422-0459-12mar-automata_hash_mapping
coursera-20130422-0459-12mar-automata_unanonymizable
coursera-20130422-0522-12mar-intrologic_anonymized_forum
coursera-20130422-0522-12mar-intrologic_anonymized_general
coursera-20130422-0522-12mar-intrologic_hash_mapping
coursera-20130422-0530-12apr-compilers_anonymized_forum
coursera-20130422-0530-12apr-compilers_anonymized_general
coursera-20130422-0530-12apr-compilers_hash_mapping
coursera-20130422-0530-12apr-compilers_unanonymizable
coursera-20130422-0632-12jan-hci_anonymized_forum
coursera-20130422-0632-12jan-hci_anonymized_general
coursera-20130422-0632-12jan-hci_hash_mapping
coursera-20130422-0632-12jan-hci_unanonymizable
coursera-20130422-0720-12-002-crypto_anonymized_forum
coursera-20130422-0720-12-002-crypto_anonymized_general
coursera-20130422-0720-12-002-crypto_hash_mapping
coursera-20130422-0809-12-002-algo_anonymized_forum
coursera-20130422-0809-12-002-algo_anonymized_general
coursera-20130422-0809-12-002-algo_hash_mapping
coursera-20130422-0919-12-002-ml_anonymized_forum
coursera-20130422-0919-12-002-ml_anonymized_general
coursera-20130422-0919-12-002-ml_hash_mapping
coursera-20130422-0919-12-002-ml_unanonymizable
coursera-20130422-0936-002-crypto_anonymized_forum
coursera-20130422-0936-002-crypto_anonymized_general
coursera-20130422-0936-002-crypto_hash_mapping
coursera-20130422-0936-002-crypto_unanonymizable
coursera-20130422-1039-005-crypto_anonymized_forum
coursera-20130422-1039-005-crypto_anonymized_general
coursera-20130422-1039-005-crypto_hash_mapping
coursera-20130422-1039-005-crypto_unanonymizable
coursera-20130422-1151-12-001-algo2_anonymized_forum
coursera-20130422-1151-12-001-algo2_anonymized_general
coursera-20130422-1151-12-001-algo2_hash_mapping
coursera-20130422-1204-12-002-gametheory_anonymized_forum
coursera-20130422-1204-12-002-gametheory_anonymized_general
coursera-20130422-1204-12-002-gametheory_hash_mapping
coursera-20130422-1206-12-003-algo_anonymized_forum
coursera-20130422-1206-12-003-algo_anonymized_general
coursera-20130422-1206-12-003-algo_hash_mapping
coursera-20130422-2135-12-001-organalysis_anonymized_forum
coursera-20130422-2135-12-001-organalysis_anonymized_general
coursera-20130422-2135-12-001-organalysis_hash_mapping
coursera-20130422-2135-12-001-organalysis_unanonymizable
coursera-20130422-2135-12-selfservice-compilers_anonymized_forum
coursera-20130422-2135-12-selfservice-compilers_hash_mapping
coursera-20130422-2135-12-selfservice-cs101_anonymized_forum
coursera-20130422-2135-12-selfservice-cs101_anonymized_general
coursera-20130422-2135-12-selfservice-cs101_hash_mapping
coursera-20130422-selfservice-compilers_anon_gen
coursera-20130430-2127-12-001-worldmusic_anonymized_forum
coursera-20130430-2127-12-001-worldmusic_anonymized_general
coursera-20130430-2127-12-001-worldmusic_hash_mapping
coursera-20130430-2127-12-001-worldmusic_unanonymizable
coursera-20130430-2128-12-001-design_anonymized_forum
coursera-20130430-2128-12-001-design_anonymized_general
coursera-20130430-2128-12-001-design_hash_mapping
coursera-20130430-2128-12-001-design_unanonymizable
coursera-20130430-2129-12-001-gamification_anonymized_forum
coursera-20130430-2129-12-001-gamification_anonymized_general
coursera-20130430-2129-12-001-gamification_hash_mapping
coursera-20130430-2129-12-001-genomescience_anonymized_forum
coursera-20130430-2129-12-001-genomescience_anonymized_general
coursera-20130430-2129-12-001-genomescience_hash_mapping
coursera-20130430-2129-12-001-genomescience_unanonymizable
coursera-20130430-2148-12-001-operations_anonymized_forum
coursera-20130430-2148-12-001-operations_anonymized_general
coursera-20130430-2148-12-001-operations_hash_mapping
coursera-20130430-2148-12-001-operations_unanonymizable
coursera-20130506-1717-compilers-003_anonymized_forum
coursera-20130506-1717-compilers-003_anonymized_general
coursera-20130506-1717-compilers-003_hash_mapping
coursera-20130506-1717-compilers-003_unanonymizable
coursera-20130531-1829-12-001-maththink_anonymized_forum
coursera-20130531-1829-12-001-maththink_anonymized_general
coursera-20130531-1829-12-001-maththink_hash_mapping
coursera-20130531-1829-12-001-maththink_unanonymizable
coursera-20130701-1010-childnutrition-001_anonymized_forum
coursera-20130701-1010-childnutrition-001_anonymized_general
coursera-20130701-1010-childnutrition-001_hash_mapping
coursera-20130701-1010-childnutrition-001_unanonymizable
coursera-20130701-1010-crypto-006_anonymized_forum
coursera-20130701-1010-crypto-006_anonymized_general
coursera-20130701-1010-crypto-006_hash_mapping
coursera-20130701-1010-crypto-006_unanonymizable
coursera-20130701-1010-democraticdev-001_anonymized_forum
coursera-20130701-1010-democraticdev-001_anonymized_general
coursera-20130701-1010-democraticdev-001_hash_mapping
coursera-20130701-1010-democraticdev-001_unanonymizable
coursera-20130701-1010-einstein-001_anonymized_forum
coursera-20130701-1010-einstein-001_anonymized_general
coursera-20130701-1010-einstein-001_hash_mapping
coursera-20130701-1010-einstein-001_unanonymizable
coursera-20130701-1010-hci-003_anonymized_forum
coursera-20130701-1010-hci-003_anonymized_general
coursera-20130701-1010-hci-003_hash_mapping
coursera-20130701-1010-hci-003_unanonymizable
coursera-20130701-1103-12-001-maththink_anonymized_forum
coursera-20130701-1103-12-001-maththink_anonymized_general
coursera-20130701-1103-12-001-maththink_hash_mapping
coursera-20130701-1103-12-001-maththink_unanonymizable
coursera-20130701-1114-pgm-003_anonymized_forum
coursera-20130701-1114-pgm-003_anonymized_general
coursera-20130701-1114-pgm-003_hash_mapping
coursera-20130701-1114-pgm-003_unanonymizable
coursera-20130701-1234-startup-001_anonymized_forum
coursera-20130701-1234-startup-001_anonymized_general
coursera-20130701-1234-startup-001_hash_mapping
coursera-20130701-1234-startup-001_unanonymizable
coursera-20130701-1256-intrologic-003_anonymized_forum
coursera-20130701-1256-intrologic-003_anonymized_general
coursera-20130701-1256-intrologic-003_hash_mapping
coursera-20130701-1256-intrologic-003_unanonymizable
coursera-20130701-1410-compilers-003_anonymized_forum
coursera-20130701-1410-compilers-003_anonymized_general
coursera-20130701-1410-compilers-003_hash_mapping
coursera-20130701-1410-compilers-003_unanonymizable
coursera-20130701-1426-12-002-compilers_anonymized_forum
coursera-20130701-1426-12-002-compilers_anonymized_general
coursera-20130701-1426-12-002-compilers_hash_mapping
coursera-20130701-1426-12-002-compilers_unanonymizable
coursera-20130701-1434-12-002-intrologic_anonymized_forum
coursera-20130701-1434-12-002-intrologic_anonymized_general
coursera-20130701-1434-12-002-intrologic_hash_mapping
coursera-20130701-1518-12-002-hci_anonymized_forum
coursera-20130701-1518-12-002-hci_anonymized_general
coursera-20130701-1518-12-002-hci_hash_mapping
coursera-20130701-1518-12-002-hci_unanonymizable
coursera-20130701-1546-12-003-crypto_anonymized_forum
coursera-20130701-1546-12-003-crypto_anonymized_general
coursera-20130701-1546-12-003-crypto_hash_mapping
coursera-20130701-1547-001-sustainableag_anonymized_forum
coursera-20130701-1547-001-sustainableag_anonymized_general
coursera-20130701-1547-001-sustainableag_hash_mapping
coursera-20130701-1547-001-sustainableag_unanonymizable
coursera-20130701-1601-12-002-pgm_anonymized_forum
coursera-20130701-1601-12-002-pgm_anonymized_general
coursera-20130701-1601-12-002-pgm_hash_mapping
coursera-20130701-1601-12-002-pgm_unanonymizable
coursera-20130701-1658-12-001-sciwrite_anonymized_forum
coursera-20130701-1658-12-001-sciwrite_anonymized_general
coursera-20130701-1658-12-001-sciwrite_hash_mapping
coursera-20130701-1658-12-001-sciwrite_unanonymizable
coursera-20130701-2048-maththink-002_anonymized_forum
coursera-20130701-2048-maththink-002_anonymized_general
coursera-20130701-2048-maththink-002_hash_mapping
coursera-20130701-2048-maththink-002_unanonymizable
coursera-20130924-1740-crypto-007_anonymized_forum
coursera-20130924-1740-crypto-007_anonymized_general
coursera-20130924-1740-crypto-007_hash_mapping
coursera-20130924-1740-crypto-007_unanonymizable
coursera-20131002-0701-ml-003_anonymized_forum
coursera-20131002-0701-ml-003_anonymized_general
coursera-20131002-0701-ml-003_hash_mapping
coursera-20131002-0701-ml-003_unanonymizable
coursera-demog-algo
coursera-demog-algo2-002
coursera-demog-algo2-2012-001
coursera-demog-algo-003
coursera-demog-algo-004
coursera-demog-algo-2012-002
coursera-demog-antimicrobial-001
coursera-demog-antimicrobial-002
coursera-demog-antimicrobial-003
coursera-demog-antimicrobial-004
coursera-demog-automata
coursera-demog-automata-002
coursera-demog-childnutrition-001
coursera-demog-clinicaltrials-001
coursera-demog-compilers
coursera-demog-compilers-003
coursera-demog-compilers-2012-002
coursera-demog-compilers-selfservice
coursera-demog-computervision-001
coursera-demog-crypto
coursera-demog-crypto2-2013-001
coursera-demog-crypto-004
coursera-demog-crypto-005
coursera-demog-crypto-006
coursera-demog-crypto-007
coursera-demog-crypto-2012-002
coursera-demog-crypto-2012-003
coursera-demog-cs101
coursera-demog-cs101-002
coursera-demog-cs101-selfservice
coursera-demog-db
coursera-demog-democraticdev-001
coursera-demog-democraticdev-002
coursera-demog-dgplay-001
coursera-demog-emscardiology-001
coursera-demog-environphys-001
coursera-demog-environphys-002
coursera-demog-gametheory
coursera-demog-gametheory-003
coursera-demog-gametheory-2012-002
coursera-demog-ggp-001
coursera-demog-hci
coursera-demog-hci-003
coursera-demog-hci-2012-002
coursera-demog-intrologic
coursera-demog-intrologic-003
coursera-demog-intrologic-004
coursera-demog-intrologic-2012-002
coursera-demog-maththink-002
coursera-demog-maththink-003
coursera-demog-maththink-2012-001
coursera-demog-ml
coursera-demog-ml-003
coursera-demog-ml-2012-002
coursera-demog-nlp
coursera-demog-nlp-002
coursera-demog-organalysis-002
coursera-demog-organalysis-2012-001
coursera-demog-palliativemed-001
coursera-demog-pgm
coursera-demog-pgm-003
coursera-demog-pgm-2012-002
coursera-demog-sciwrite-2012-001
coursera-demog-security
coursera-demog-startup-001
coursera-demog-startup-002
coursera-demog-vidmooc-001
coursera_2012_cs101_anonymized_general
coursera_2012_cs101_hash_mapping
coursera_2012_cs101_pii
coursera_2012_db_anonymized_general
coursera_2012_db_hash_mapping
coursera_2012_db_pii
coursera_2012_hci_anonymized_forum
coursera_2012_hci_anonymized_general
coursera_2012_hci_hash_mapping
coursera_2012_hci_pii
coursera_2012_hci_unanonymizable
coursera_2012_logic_anonymized_forum
coursera_2012_logic_anonymized_general
coursera_2012_logic_hash_mapping
coursera_2012_logic_pii
coursera_2012_maththink_anonymized_forum
coursera_2012_maththink_anonymized_general
coursera_2012_maththink_hash_mapping
coursera_2012_maththink_pii
coursera_2012_maththink_unanonymizable
coursera_2012_ml_anonymized_forum
coursera_2012_ml_anonymized_general
coursera_2012_ml_hash_mapping
coursera_2012_ml_pii
coursera_2012_ml_unanonymizable
coursera_2012_pgm_anonymized_forum
coursera_2012_pgm_anonymized_general
coursera_2012_pgm_hash_mapping
coursera_2012_pgm_pii
coursera_2012_pgm_unanonymizable
coursera_2012_sciwri_anonymized_forum
coursera_2012_sciwri_anonymized_general
coursera_2012_sciwri_hash_mapping
coursera_2012_sciwri_pii
coursera_2012_sciwri_unanonymizable
coursera_eventing_001-sustainableag
coursera_eventing_002-crypto
coursera_eventing_005-crypto
coursera_eventing_12-001-algo2
coursera_eventing_12-001-maththink
coursera_eventing_12-001-organalysis
coursera_eventing_12-001-sciwrite
coursera_eventing_12-002-algo
coursera_eventing_12-002-compilers
coursera_eventing_12-002-crypto
coursera_eventing_12-002-gametheory
coursera_eventing_12-002-hci
coursera_eventing_12-002-intrologic
coursera_eventing_12-002-ml
coursera_eventing_12-002-pgm
coursera_eventing_12-003-algo
coursera_eventing_12-003-crypto
coursera_eventing_Machine Learning (ml-003)_clickstream_export
coursera_eventing_childnutrition-001
coursera_eventing_compilers-003
coursera_eventing_crypto-006
coursera_eventing_democraticdev-001
coursera_eventing_einstein-001
coursera_eventing_intrologic-003
coursera_eventing_maththink-002
coursera_eventing_pgm-003
coursera_eventing_startup-001
OpenEdx Hosted
Edx
ExPrivate
NovoEd Hosted Databases
novoed-crs_23_ACrashCourseonCreativity
novoed-crs_24_TechnologyEntrepreneurshipPart1
novoed-crs_25_Finance
novoed-crs_29_OrganizationalBehavior
novoed-crs_30_HippocratesChallenge
novoed-crs_46_DesignThinkingActionLab
novoed-crs_ACrashCourseonCreativity
novoed-crs_AdvancedEntrepreneurship
novoed-crs_BusinessManagementforEEandCSStudents
novoed-crs_DesigningaNewLearningEnvironment
novoed-crs_EntrepreneurshipinEnvironmentalEngineering
novoed-crs_Finance
novoed-crs_GraphPartitioningandExpanders
novoed-crs_MobileHealthWithoutBorders
novoed-crs_OrganizationalBehavior
novoed-crs_StartupBoards
novoed-crs_SustainableProductDevelopment
novoed-crs_Technology_Entrepreneurship
novoed-crs_email_23_ACrashCourseonCreativity
novoed-crs_email_24_TechnologyEntrepreneurshipPart1
novoed-crs_email_25_Finance
novoed-crs_email_29_OrganizationalBehavior
novoed-crs_email_30_HippocratesChallenge
novoed-crs_email_46_DesignThinkingActionLab
novoed-crs_email_ACrashCourseonCreativity
novoed-crs_email_AdvancedEntrepreneurship
novoed-crs_email_BusinessManagementforEEandCSStudents
novoed-crs_email_DesigningaNewLearningEnvironment
novoed-crs_email_EntrepreneurshipinEnvironmentalEngineering
novoed-crs_email_Finance
novoed-crs_email_GraphPartitioningandExpanders
novoed-crs_email_MobileHealthWithoutBorders
novoed-crs_email_OrganizationalBehavior
novoed-crs_email_StartupBoards
novoed-crs_email_SustainableProductDevelopment
novoed-crs_email_Technology_Entrepreneurship
vl_2013_boards
vl_2013_creativity
vl_2013_education
vl_2013_finance
vl_2013_venture
Appendix B: How to Set up an SSH Tunnel
An ssh tunnel is a connection between two computers that encrypts the
information it carries. Sometimes a server machine is running a
service that client applications on another machine can connect
to. For example, Excel connecting directly to a MySQL database is such
an example. Similarly, Froq and RazorSQL, the graphical querying tools
mentioned earlier, might connect directly from your computer to the
MySQL database that runs on the datastage.stanford.edu machine.
This style of direct connection has your password go over the Internet
unencrypted when you log into the database. This vulnerability to wire
tapping is a disadvantage of direct connections. On the other hand,
setting up a direct connection is relatively easy, and client side
applications, the programs you use on your computer to connect to the
database, know how to construct a direct connection.
To protect data more securely, a tunnel may first be
constructed between your computer and the database server
computer. Your commands to the database then first travel encrypted to
the server computer through the tunnel. Once they arrive, the commands
are handled as if they had been issued on the server computer itself
in the first place.
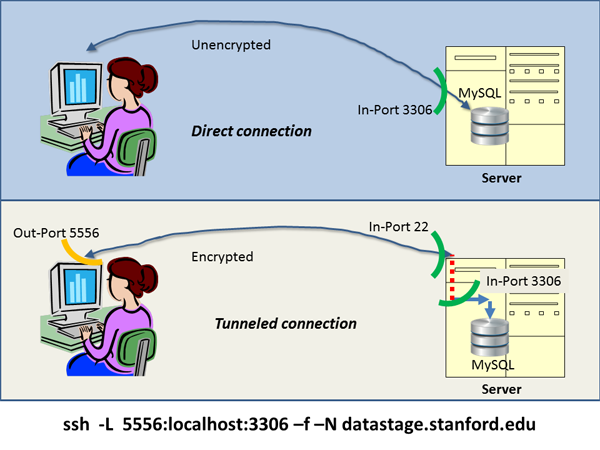 To set up a tunnel between your computer and datastage.stanford.edu,
you type the command at the bottom of the illustration into a terminal
window before you ask your data access application to try and
get to the data. The command says: set up a secure connection
(ssh) to machine datastage.stanford.edu; to applications
on my own computer the connection is to look like a database to which
I write via my out-port 5556. The connection should function
like a tunnel (-L). On the database on the other end, the
commands I send should look like they were issued on its
machine (localhost from the database's point of view), and were
issued directly into the in-port where the database normally listens
to (3306), as it does in the direct connection case.
The -f -N just make it so that you can keep using the terminal
window you used to type in the command.
Important point: in order to get into that in-port 22 in the figure,
you will need a password; the same password you would need to log into
that machine. In order to get through the in-port 3306 into the
database within the server, you will need a second password, the one
that authenticates you to the database. You would need that one in the
direct connection as well, unless the database maintainer has not set
a password for you.
To set up a tunnel between your computer and datastage.stanford.edu,
you type the command at the bottom of the illustration into a terminal
window before you ask your data access application to try and
get to the data. The command says: set up a secure connection
(ssh) to machine datastage.stanford.edu; to applications
on my own computer the connection is to look like a database to which
I write via my out-port 5556. The connection should function
like a tunnel (-L). On the database on the other end, the
commands I send should look like they were issued on its
machine (localhost from the database's point of view), and were
issued directly into the in-port where the database normally listens
to (3306), as it does in the direct connection case.
The -f -N just make it so that you can keep using the terminal
window you used to type in the command.
Important point: in order to get into that in-port 22 in the figure,
you will need a password; the same password you would need to log into
that machine. In order to get through the in-port 3306 into the
database within the server, you will need a second password, the one
that authenticates you to the database. You would need that one in the
direct connection as well, unless the database maintainer has not set
a password for you.
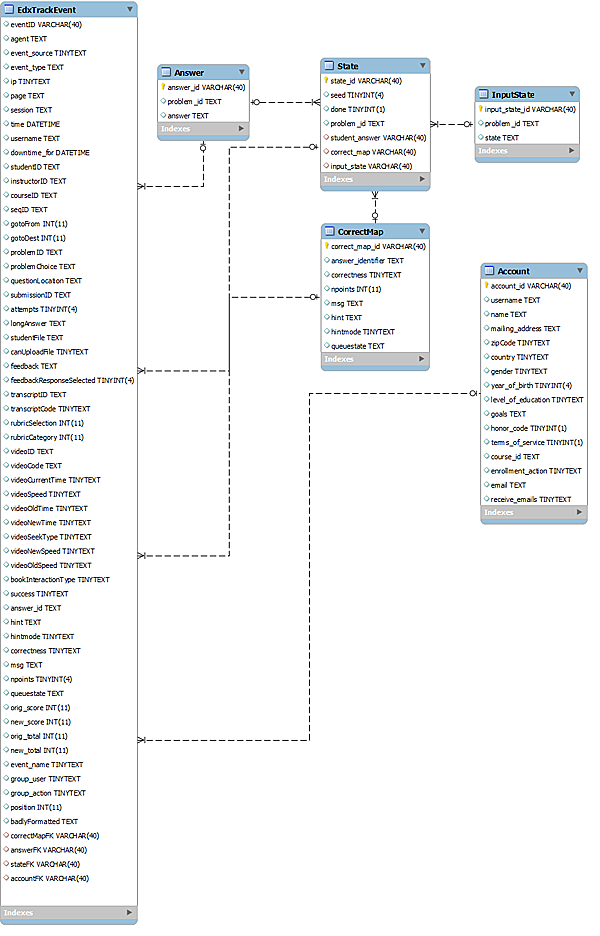
Appendix C: Edx and EdxPrivate ER Diagram